In an age of mobile driver’s licenses and digital passports, the term “digital identity” has taken on a much broader meaning. Once considered just a technical component of information systems, it has become a critical asset for individuals, businesses, and governments—and one that must be safeguarded with the highest level of security.
This article explores how digital identity has evolved over time, how it is applied today, the key threats it faces, and where it’s headed next.
At its core, a digital identity is a collection of attributes in a digital environment that represent a specific entity—a person, device, application, endpoint, or even an entire organization. These attributes, or identifiers, are what systems use to tell entities apart.
• For machines, an IP address might be enough.
• For people, it could be as simple as an email address and password.
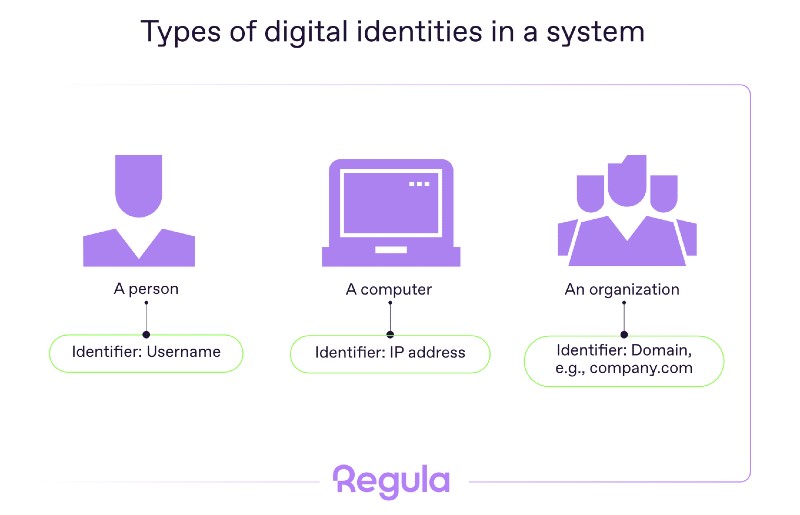
However, digital identity is not the same as a user. A user is a broader concept, tied to an access hierarchy. The higher a user’s authorization, the more system resources they can reach. For example, in a marketplace, an admin can manage the entire platform, while a regular user may only log in, shop, or edit their profile.
Importantly, non-human actors like servers or software can also hold digital identities. But for the purpose of this article, we’ll focus on human identities.
To function properly, digital identities and their identifiers are stored and managed in identity and access management (IAM) systems. IAM frameworks rely on two main processes:
• Authentication: confirming that someone is who they claim to be.
• Authorization: determining what they’re allowed to access.
Identifiers generally fall into three categories:
1. Inherent — permanent traits like biometrics (fingerprint, facial scan, iris pattern).
2. Assigned — identifiers granted by third parties (passport number, SSN, mobile number, username, email).
3. Accumulated — behavioral data collected over time (login history, IP addresses, purchase behavior, edits to a profile).
In practice, systems often combine these identifiers. A simple login may use just a username and password, while a banking app might add SMS codes or biometrics for extra security.
Traditional password-only access is now considered the weakest method. Stronger approaches include:
• Two-factor authentication (2FA) — pairing a password with an additional identifier like a one-time code.
• Biometric checks — facial scans or fingerprint recognition, often paired with liveness detection to prevent spoofing.
With more than 5.5 billion internet users worldwide, each maintaining multiple accounts, the number of digital identities is staggering. They can be grouped into three broad levels:
1.Personal identities — created voluntarily for communication or entertainment (e.g., social media, dating apps). These may be fully anonymized or closely tied to a real individual.
2. Commercial identities — required to access services such as online banking, e-commerce, or telecom. These usually involve stronger identifiers, often regulated under KYC/AML frameworks.
3. Governmental identities — mandated by public institutions for tax filing, benefits, or healthcare. They require comprehensive personal data and often include biometric elements.
Across these levels, there is usually a trade-off: the more secure an identity is, the less anonymous it becomes.
Here, users control how much of themselves they reveal—anything from pseudonyms to full personal details. Unfortunately, many rely on weak identifiers like simple passwords. As a result, personal accounts are frequent targets for breaches: more than 16 billion credentials have been exposed in recent years.
Businesses such as banks and fintechs enforce stricter requirements. A mobile banking app, for example, may require a password, identity document, and a selfie check. Beyond that, customer behavior is monitored as an additional safeguard.
Still, the level of protection varies by industry and geography. Some countries, like the UAE, are moving toward unified KYC platforms, while others maintain sector-specific rules.
Emerging models like verifiable credentials (cryptographically signed attributes, such as “is over 18” or “holds a driver’s license”) and reusable identities (wallet-based profiles used across services) are changing how people manage their commercial identities.
Governments maintain fully deanonymized digital identities linked to official registries. These are used for public services, tax filing, or healthcare access. Security frameworks differ by country.
• In Australia, the myID platform offers three tiers of identity strength, from basic details to full document and biometric verification.
• In China, users receive a unique internet ID number after registering with physical documents, linking their digital and real identities.
• In the EU, the eIDAS framework is creating digital identity wallets that let users control their data across borders, with full rollout expected by 2026.
The most recent step in this evolution is the replacement of physical documents with digital IDs, usable for both online and in-person verification.
Despite their benefits, digital identities remain vulnerable across all levels. The biggest risks include:
1. Identity fraud — from phishing and account takeovers to deepfake-based impersonation, synthetic identities, and document forgeries. These attacks threaten individuals with financial loss, businesses with compliance penalties, and governments with national security risks.
2. Poor digital hygiene — weak passwords, reusing credentials, and skipping multi-factor authentication. Awareness campaigns help, but mandatory security measures like biometric checks are often more effective.
3. Technical and privacy challenges — new identity models require global interoperability. Yet trust between governments, businesses, and users is fragile, and infrastructure upgrades are necessary to support secure cross-border verification.
Digital identity has come a long way from its origins as a technical construct. Today, it underpins ecosystems spanning personal accounts, global commerce, and government services. The challenge now lies in building systems that are secure, interoperable, and trusted by all stakeholders.
Trust, however, cannot be scaled—it must be earned through accuracy, reliability, and compliance.
As a global leader in identity verification, Regula provides solutions that ensure security without friction:
• Document Reader SDK — customizable, border-level document verification for both online and offline scenarios.
• Face SDK — advanced facial recognition with built-in liveness detection, protecting against spoofing and presentation attacks.
Trusted by banks, airlines, border controls, and fintechs worldwide, Regula helps institutions build the foundation of a secure digital identity ecosystem.
The post The evolution and future of digital identity appeared first on BusinessCloud.
Also read: Federal Judge Blocks Trump From Removing Fed Governor Lisa Cook