In proof-of-stake blockchains, slashing is often mentioned with a hint of fear. But for regular users, the chance of being slashed is almost zero. Delegators only face small risks if their chosen validator misbehaves. For validators, however, slashing is a built-in safeguard that enforces the network’s rules and deters inefficient or dishonest behavior.
In order to better understand your risks when staking crypto, it is important to know what slashing is and how it works.
Slashing refers to a penalty mechanism used in proof-of-stake (PoS) blockchains to discourage dishonest or negligent behavior by validators. Validators are responsible for confirming transactions and securing the network. If they act against the rules, no matter if intentionally or accidentally, the protocol can “slash” them by taking away part of their staked tokens.

The main goal of slashing is to align validator incentives with network security. Since validators must lock up tokens as collateral, they risk losing money if they fail to act properly. This ensures that only those committed to honest participation remain in the validator set.
Not every PoS blockchain uses the slashing mechanism, but for those that do, it plays a critical role in keeping the network secure, fair, and resistant to attacks.
Read more: Proof-of-Stake vs. Proof-of-Work Blockchains.
The concept of slashing emerged alongside (and, in a way, as a consequence of) the development of proof-of-stake blockchains. Early PoS designs in the 2010s focused on energy efficiency and token-based security but lacked strong deterrents for dishonest validators. Without meaningful penalties, malicious actors could disrupt consensus with little downside.
Ethereum researchers popularized slashing during the shift to Ethereum 2.0, where it became a core part of validator accountability. The network introduced penalties not only for inactivity but also for harmful behaviors like double-signing or colluding in consensus attacks.
Other ecosystems, such as Cosmos and Polkadot, adopted similar frameworks, each tailoring slashing rules to their consensus models. Over time, slashing has become a standard tool in many PoS blockchains, reinforcing security by making bad behavior costly.
Slashing serves multiple purposes in proof-of-stake blockchains. It is not only a punishment but also a deterrent and an incentive mechanism that ensures validators act in the best interest of the network.
Slashing makes attacks costly. Validators who attempt double-signing, collusion, or consensus manipulation risk losing their stake. This high financial penalty discourages malicious actors from trying to undermine the system.
Validators must operate reliable nodes and follow protocol rules. If they fail, whether through negligence, downtime, or mismanagement, they face penalties. This creates accountability and filters out validators who cannot maintain proper operations.
By punishing harmful or careless actions, slashing strengthens network security. It reduces the chance of forks, chain instability, or coordinated attacks, preserving trust in the blockchain’s consensus.
Slashing ensures that all validators play by the same rules. Honest validators are rewarded, while dishonest or careless ones are penalized. This levels the playing field and fosters confidence among delegators who stake their tokens with validators.
Learn how to spot scams and protect your crypto with our free checklist.

Slashing relies on a set of roles, rules, and processes that together enforce good behavior in proof-of-stake networks. At the center of this system are validators, delegators, and, in some protocols, whistleblowers.
Read more: What Is Crypto Staking?
Once a violation is confirmed, the slashing process begins. Depending on the blockchain, penalties can range from small stake deductions for downtime to severe measures such as permanent validator removal, token burns, or redistribution of slashed funds to the treasury. Some systems also impose “jail time,” where a validator is barred from participating for a period before they can return.
Economic parameters determine the impact of slashing. These include the slashing fraction (how much stake is cut per offense) and correlated slashing, where penalties increase if many validators misbehave at the same time, deterring coordinated attacks. Protocol rules also tie in governance: communities can adjust slashing conditions through on-chain voting, and funds collected may flow into the network’s treasury.
To avoid unnecessary penalties, validators rely on technical safeguards like slash protection databases, remote signers that keep keys isolated from machines, and secure setups such as sentry node architecture. Best practices in monitoring, alerting, and key management further reduce risks.
Validators can be penalized for several types of misbehavior in proof-of-stake (PoS) networks. These actions, among other things, can threaten the network’s consensus process or disrupt the chain’s transaction history. The exact rules vary across PoS protocols and delegated proof-of-stake systems, but the main categories of slashing events are consistent.
Double signing happens when a validator signs two different blocks for the same slot or height. This creates conflicting versions of the network’s transaction history. In PoS networks, such behavior is treated as a serious violation because it could lead to forks and loss of trust in the chain. Validators caught double signing are usually slashed heavily.
Surround voting occurs when a validator submits one vote that overlaps or “surrounds” another vote they previously signed. This undermines the consensus process by introducing contradictory attestations. Proof-of-stake protocols like Ethereum explicitly penalize this behavior, since it can be used to manipulate finality.
Validators must stay online to produce blocks and validate transactions. If a validator remains offline for too long—whether due to poor infrastructure, network issues, or negligence—they may be slashed. In delegated proof-of-stake systems, downtime penalties also affect delegators who staked with that validator. While downtime is less severe than double signing, it still harms the network’s liveness.
Some slashing conditions target broader attempts to manipulate consensus, such as colluding with other validators to change transaction ordering or stall block production. These attacks threaten both safety and fairness in PoS protocols. Slashing ensures such coordinated efforts are extremely costly, discouraging validators from undermining the network’s integrity.
When a validator is slashed, the penalty is applied automatically by the network’s protocol. The impact depends on the severity of the violation, but the process usually follows the same sequence.
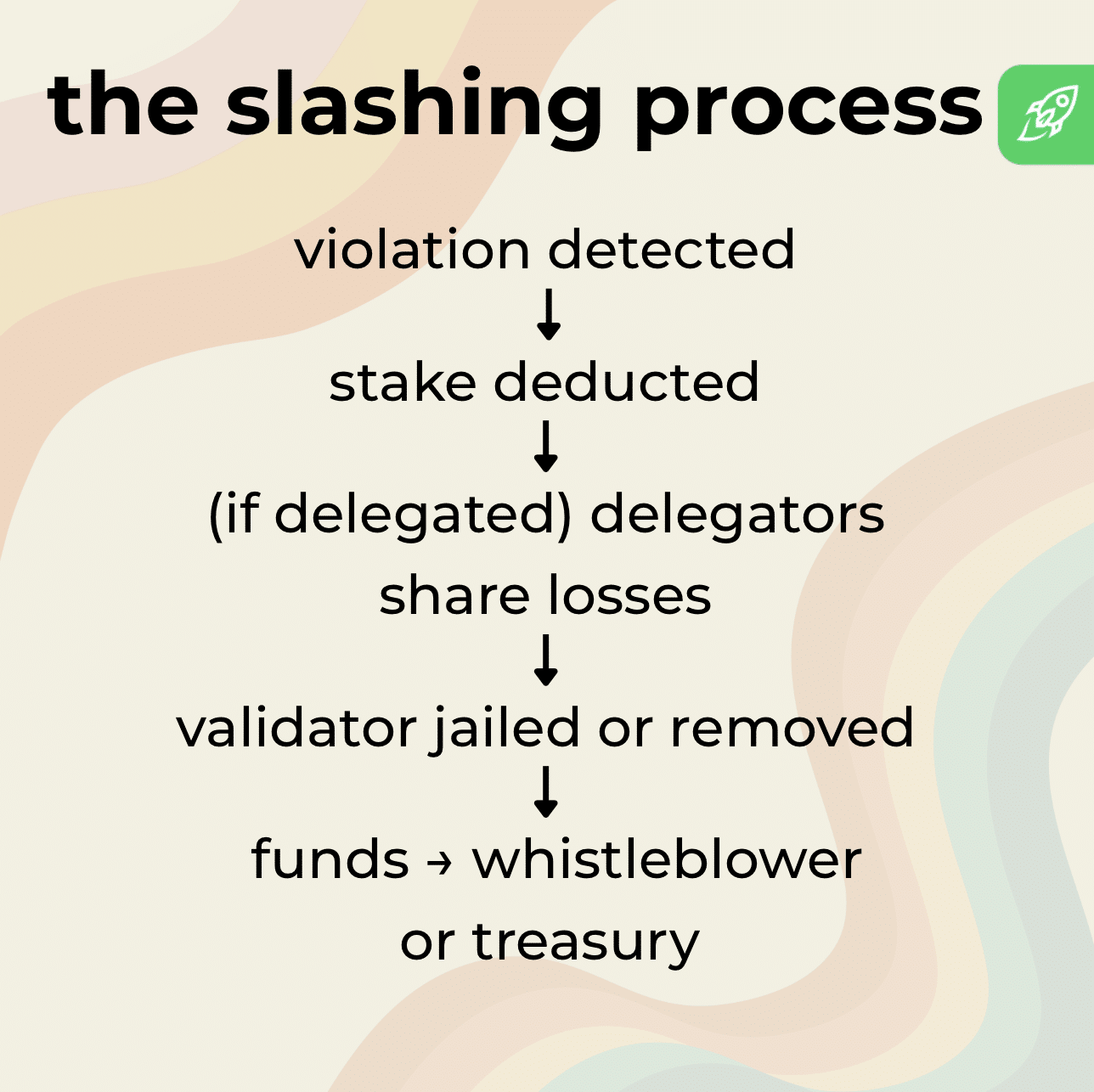
This creates immediate financial consequences and, in many cases, reputational damage: delegators are less likely to trust a validator with a history of penalties.
Slashing rules vary across PoS networks, but the goal is the same: to secure consensus and deter validator misbehavior. Here’s how some major blockchains handle it:
Ethereum penalizes validators for double signing, surround voting, and extended downtime. Severe offenses can lead to validator ejection. Penalties scale with how many validators misbehave at once (correlated slashing).
In Polkadot, slashing applies to validators and nominators. Offenses include equivocation (double signing) and unresponsiveness. Penalties range from small deductions to removal from the active set, with slashed funds going partly to the treasury.
Cosmos slashes validators for double signing and downtime. Delegators also share in the penalties, reinforcing the need to choose validators carefully. Severe cases lead to “tombstoning,” which permanently removes the validator.
Tezos slashing is focused on double baking (proposing two blocks at the same height) and double endorsing (signing conflicting blocks). Misbehaving validators lose part of their bond, and delegators are indirectly impacted through reduced rewards.
Not all blockchains use slashing. Different consensus mechanisms enforce validator or miner discipline in different ways. In proof-of-stake (PoS) networks, penalties usually involve stake reduction, while in proof-of-work (PoW) systems, the cost comes from wasted energy and resources.
Slashing targets malicious or negligent behavior, but both validators and delegators can take steps to minimize risks.
Slashing can be a rather controversial topic in the crypto community. On one hand, penalizing validators can feel harsh, especially when downtime or mistakes cause honest operators to lose funds. Critics argue that it can discourage smaller participants who lack the resources to run highly redundant systems.
On the other hand, facts show that slashing is an effective safeguard. By enforcing strict network rules, it deters malicious or negligent behavior and prevents validators from undermining consensus. Without it, PoS networks would be more vulnerable to forks, collusion, and inefficient behavior that weakens security.
In practice, most major proof-of-stake protocols rely on slashing because the benefits outweigh the risks. It keeps validators accountable and reassures delegators that the network has strong defenses in place.
Slashing is more than just a punishment: it’s a design choice that balances incentives, strengthens security, and ensures fairness in proof-of-stake systems. By penalizing validators for malicious or inefficient behavior, networks protect both their consensus and their users.
For everyday token holders, the main takeaway is simple: pick validators carefully, stay informed about the rules of the chain you’re participating in, and slashing will likely never affect you directly. For validators, the message is stricter: follow protocol rules, operate reliable nodes, and treat security as a priority.
As proof-of-stake continues to expand, slashing will remain a cornerstone of how blockchains enforce trust without central authorities.
No. Some networks choose softer penalties or rely only on reward reduction, but many adopt slashing to enforce their own rules and discourage bad behavior.
Slashing is relatively rare. Most validators follow the rules, and modern setups include protections that minimize slashing risks.
Check validator performance, uptime, and history. Delegating to operators with a proven track record reduces the chance of losses if slashing occurs.
Disclaimer: Please note that the contents of this article are not financial or investing advice. The information provided in this article is the author’s opinion only and should not be considered as offering trading or investing recommendations. We do not make any warranties about the completeness, reliability and accuracy of this information. The cryptocurrency market suffers from high volatility and occasional arbitrary movements. Any investor, trader, or regular crypto users should research multiple viewpoints and be familiar with all local regulations before committing to an investment.
The post What Is Slashing in Crypto? How It Works and Why It Matters appeared first on Cryptocurrency News & Trading Tips – Crypto Blog by Changelly.
Also read: Binance Launches P2P Safety Education Campaign