
This warning comes after a group of security researchers called SEAL published details about 60 fake worker profiles connected to North Korea.
On September 17-18, 2025, CZ posted on social media platform X about the growing problem. He explained how these hackers are getting smarter and more patient in their attacks on crypto companies.
CZ outlined four main ways these hackers try to break into companies:
Fake Job Applications: The hackers apply for real jobs at crypto companies, especially targeting developer, security, and finance positions. Once they get hired, they have access to company systems from the inside.
Interview Tricks: They pretend to be employers conducting job interviews with employees from other companies. During video calls, they claim there’s a problem with Zoom and send a link for an “update.” This link actually contains a virus that takes over the person’s computer.
Malicious Code: These hackers give people coding challenges and then send “sample code” that contains hidden malware. When someone runs this code, it infects their system.
Bribery: They offer money to employees and contractors to get access to sensitive company data. CZ mentioned that a recent hack of an Indian outsourcing company led to over $400 million in losses at a major U.S. crypto exchange.
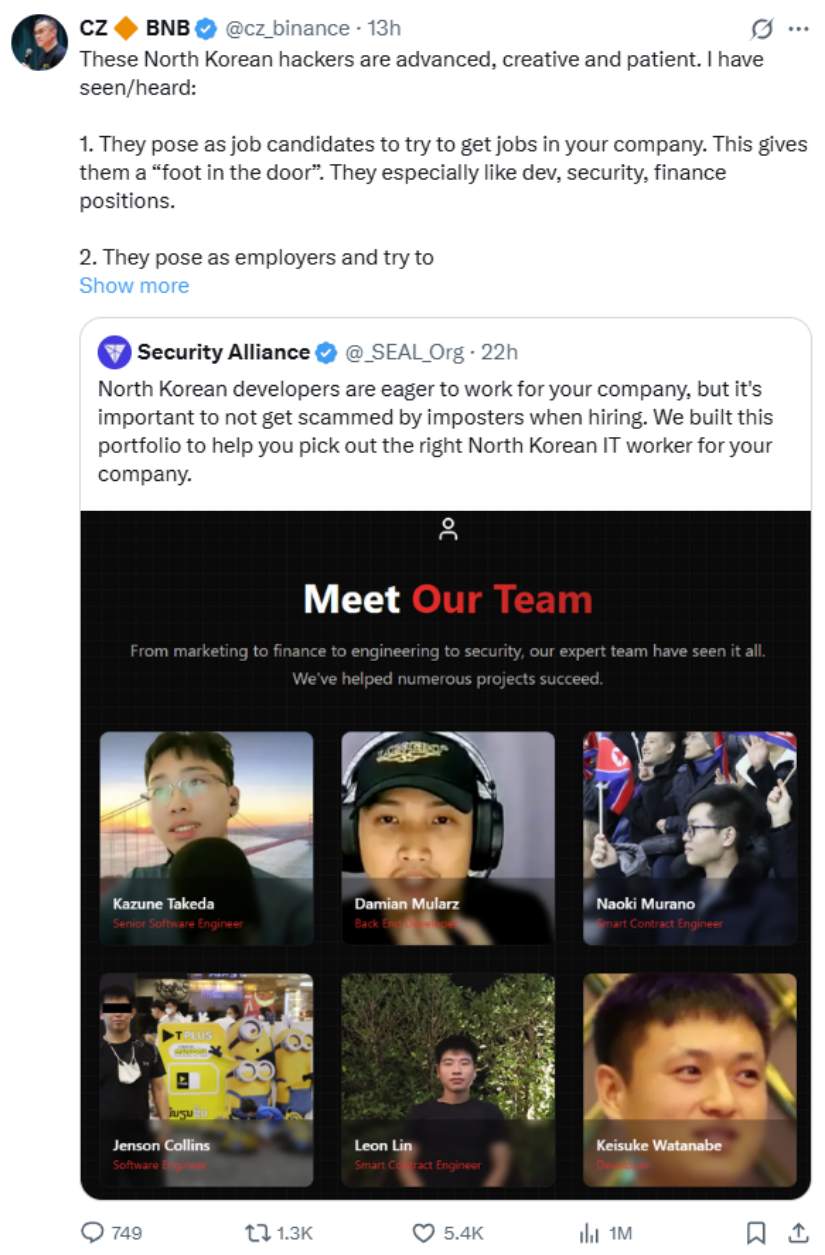
The Security Alliance (SEAL), a team of ethical hackers led by researcher Samczsun from Paradigm, has been tracking these fake workers. They created a public database at lazarus.group/team that shows 60 different fake profiles used by North Korean operatives.
Source: @cz_binance
This database includes fake names, email addresses, fake citizenship documents, and even shows which companies hired these imposters. One example profile shows “Kazune Takeda,” listed as a Senior Software Engineer who was hired by two different companies.
The SEAL team has conducted over 900 investigations in the past year, showing how big this problem has become for the crypto industry.
North Korean hackers had their biggest year ever in 2024. According to Chainalysis data, these groups stole $1.34 billion worth of cryptocurrency across 47 different attacks. This amount represents 61% of all crypto stolen worldwide in 2024.
This is more than double what they stole in 2023, when North Korean hackers took $660 million across 20 incidents. The total global crypto theft reached $2.2 billion in 2024, a 21% increase from the previous year.
Some of the biggest attacks included:
DMM Bitcoin lost $305 million worth of Bitcoin in May 2024
WazirX, an Indian exchange, lost $230 million in July 2024
Multiple smaller attacks targeting various crypto startups
These hackers are part of groups connected to North Korea’s government, including the famous Lazarus Group. The stolen money helps fund North Korea’s weapons programs and helps the country avoid international sanctions.
Major crypto companies are taking action to protect themselves. Coinbase now requires all new employees to complete training in person in the United States. Workers who handle sensitive systems must be U.S. citizens and provide fingerprints.
Coinbase CEO Brian Armstrong explained the scale of the problem, saying it feels like “500 new people graduating every quarter from some kind of school they have, and that’s their whole job.”
In July 2025, U.S. citizen Christina Marie Chapman was sentenced to 8.5 years in prison for helping North Korean hackers get jobs at American companies using fake identities. This case shows how some people inside the U.S. are helping these foreign hackers.
Something interesting happened in mid-2024 that changed North Korean hacking patterns. After Russian President Vladimir Putin met with North Korean leader Kim Jong Un in June 2024, the amount of crypto stolen by North Korean hackers dropped by about 54%.
This decline happened because Russia started giving North Korea money and weapons for other activities, including sending North Korean soldiers to fight in Ukraine. When North Korea had other ways to make money, they seemed to focus less on crypto theft.
However, security experts warn that this could be temporary. The hackers are still active and continue to develop new ways to attack crypto companies.
These attacks go beyond just stealing money. U.S. and international officials say North Korea uses stolen cryptocurrency to fund its nuclear weapons and missile programs. Reports suggest that crypto theft funds about half of North Korea’s missile development.
The hackers are also getting better at using new technology. They now use artificial intelligence to create fake profile photos and even use deepfake technology during video interviews to fool hiring managers.
CZ warned all crypto platforms to train their employees not to download unknown files and to carefully check all job candidates. He stressed that these hackers are “advanced, creative, and patient” – making them particularly dangerous.
The developer community has also been targeted, with North Korean hackers posing as recruiters on LinkedIn and sending coding assignments that contain hidden malware.
The crypto industry is fighting back with better security measures, employee training, and cooperation with law enforcement. The SEAL team’s work in exposing these fake profiles gives companies a valuable tool to check potential employees.
Companies are also implementing stricter hiring practices, requiring in-person meetings, and using better background checks. Some are working directly with the FBI’s North Korea cyber unit to share information about attacks.
Also read: 88% of NFT Airdrops Lose Value Shortly After Launch – DappRadar